There was an email in my inbox from Commercial Observer (a commercial real estate industry newsletter/magazine), including links to an article titled “SHED Pitches Itself as an Affordable Scaffolding Alternative to Urban Umbrella”. For those who don’t know, sidewalk scaffolding, or sidewalk sheds, are required under New York City Local Law 11, which mandates that building facade inspections and repairs be done every 5 years (for buildings over 6 stories), and that during that work, pedestrians must be protected by erection of a protective shed. Most of these are ugly steel pipe and plywood monstrosities. Urban Umbrella found a niche to create nicer looking structures (albeit at a hefty price), and now SHED is looking for an opportunity to make inroads into their segment by making nicer looking structures, cheaper. That’s in a nutshell the article.
From there, to a related article in BusinessWire, “Urban Umbrella Raises $6.5M in Venture Debt Funding Round.” I was curious as to just how big a business this is, so I thought I’d read this article. But the article was hard to read. The font, just… all of it. So I switched to “Reader view” (I’m on Safari, on a Mac, the the same simplified reader mode exists in numerous browsers for all platforms, as far as I know).
This was better, easier to read. Still, the font choices were not what I wanted. Apple (in this case) makes several available, including Athelas, Charter, Georgia, Iowan, New York, Palatino, etc., but does not include any dyslexia-specific font (I am not specifically dyslexic, but I nevertheless find myself able to read web content faster and absorb it better when using a dyslexic-tuned font like “OpenDyslexic”).
There used to be a way to add your own font to the list of choices (or to force it to use a specific one that is not on the list). I couldn’t find or remember how to do that, so I looked it up. I found one reference that indicated where the file was that controlled the appearance of Reader view, and that perhaps editing that file could bring about the desired results, if it was in fact editable.
I didn’t realize at first how old the reference was – over 10 years – and so the location of the file turned out not to be where the article suggested. It was given as “/System/Library/PrivateFrameworks/Safari.framework/Versions/A/Resources”. Ok, so I’ll go there. They missed a node, as there is also the language-specific folder, in my case en.lproj, in which I would expect to find the file. It wasn’t there.
But I noticed, at the top of the folder, an interesting-looking file, called DiffieHellmanErrorPage.html. Hmmm. What the heck is DiffieHellman? Or who is Diffie Hellman?
It turns out that “the Diffie-Hellman algorithm was a stunning breakthrough in cryptography that showed cryptographic keys could be securely exchanged in plain sight,” according to an InfoWorld article that I found. Ahhh! This is something I’ve always been interested in, and never really understood. I thought I’d like to know, so I read the article. It seemed to be written pretty accessibly.
The article itself contained a few mistakes. Two images were identical and should have been different, one other picture was missing entirely, a typo created confusion in reading part of the explanation, there’s a broken link to an external web page, and there’s a section that should have been entitled “and then a miracle occurs,” because it didn’t explain, in the end, how the “private” part of the public-private key is able to be used in public but remain private. I still don’t get it. So of course I wrote to the article’s author indicating these issues, and I await his no-doubt considered response.
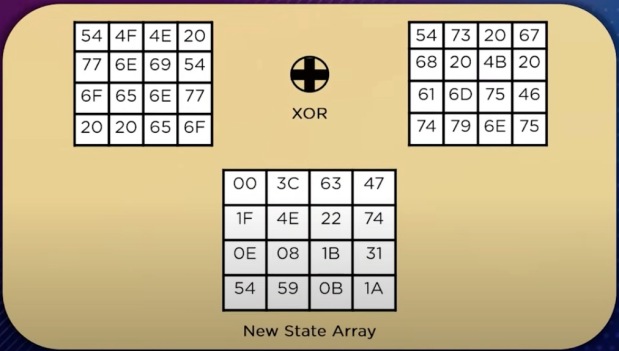
Meanwhile, I would try to find out some things on my own, regarding this public-private key business. So on to AES, the Advanced Encryption Standard, or the Rijndael block cipher standard. Digging deeper and deeper, I had to relearn what XOR does. Then on to SubBytes (what are these?), ShiftRows (how does this work?), MixColumns (how does this work?), and AddRoundKey (as I said, how does this work?). There are numerous examples of “how does this work” on pages available online, and most have some type of continuity error in them. For example, they start out defining a matrix in a certain way, and then perhaps quoting from a different source, all of a sudden are defining it a different way. Very frustrating and confusing. But through persistent searching, I finally found one that seemed to reveal it by relying on examples, where we are actually walking through each step, in plain text, hexadecimal, and binary, to show how each step works. This is the one that I was finally able to follow. (Wanna see it?)
Still, questions remained. How is the S-Box created? There are rules that govern how it is built, and I don’t know who builds it, or how. For example, in the example, 20 becomes B7, 46 becomes 5A, 67 becomes 85, etc. Is this always the case? Otherwise, how do both “authorized parties” know the substitution (i.e., sender and receiver, to the exclusion of any eavesdroppers)?
In another step of the AES, there’s this MixColumns, and for that, there’s a “fixed matrix” that gets multiplied against the current “State Matrix” after each round of encryption. Again, where does that fixed matrix come from? Is it always the same, or is it always different? If it’s always the same, how does that step make things more complex? And if it’s always different, how do both sides know what it is?
To be honest, I now have a better understanding for how the stuff is encrypted into what appears like gibberish to everyone who does not have the key. I’m missing those two parts, on the S-box and the fixed matrix, but ok, I kind of get what they’re doing here. The end result is really profoundly different from what the original was. That’s good. But I still don’t actually understand how the other side is able to decrypt it, without any transfer of the key ever being made in a publicly accessible channel. And yet, somehow, it happens, for every online transaction we all make every day, for every encrypted message we send. I don’t know how both sides are able to share information, without telling each other what the code is. I don’t get it.
And in the end, where have I gone, and how did I get here? I only wanted to read an article about scaffolding; part of my daily roundup of vaguely industry-relevant news. And look where I’ve ended up. It actually took me a while to remember how I even got started down this rabbit hole in the first place!
But if my boss asks me why I haven’t gotten any work done today, at least I can point to this. I think this explains the whole reason, in painful detail.
(Of course, add to this the fact that I had to write down this explanation, and then post it to WordPress. But we can gloss over these latter two.)